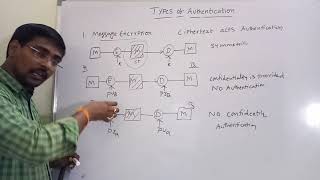
TYPES OF AUTHENTICATION || MESSAGE ENCRYPTION || MESSAGE AUTHENTICATION CODE || HASH FUNCTIONS
Similar Tracks
SHA-512 ALGORITHM || SECURE HASH ALGORITHM || CRYPTOGRAPHIC HASH FUNCTIONS || NETWORK SECURITY
t v nagaraju Technical
Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
Simplilearn
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability
IBM Technology
NETWORK SECURITY - TYPES OF AUTHENTICATION (Message Encryption, MAC, Hash Functions)
Sundeep Saradhi Kanthety